In the fast-paced realm of business, uncertainties are inevitable. From market fluctuations to unforeseen challenges, every venture encounters risks that can potentially impact its success. To mitigate these risks effectively, businesses employ a strategic approach called Risk Management. In this blog, we will explore how risks in business are identified, documented within a risk register, and assessed using a risk score matrix, ultimately ensuring a resilient and adaptive business model.
Identifying Risks: The Foundation of Risk Management
Identifying risks is the first crucial step in the risk management process. Businesses need to be vigilant in recognising potential threats that could hinder their objectives. Risks can stem from various sources such as financial instability, technological vulnerabilities, legal issues, or even natural disasters. Through thorough analysis and scenario planning, businesses can anticipate these risks and prepare proactive strategies.
Documenting Risks: The Risk Register
Once risks are identified, it is imperative to document them systematically. The tool commonly used for this purpose is a Risk Register. A Risk Register is a detailed document that compiles all identified risks, their potential impact, and the strategies devised to mitigate them. Each risk is carefully categorised, providing a comprehensive overview for stakeholders. This document serves as a roadmap for risk management efforts, enabling businesses to stay organised and focused on addressing potential challenges. The Risk Register should align with the RIsk components within the project RAID Logs. The Risk Register should also be covered as a standard agenda item for Board meetings.
Assessing Risks: The Risk Score Matrix
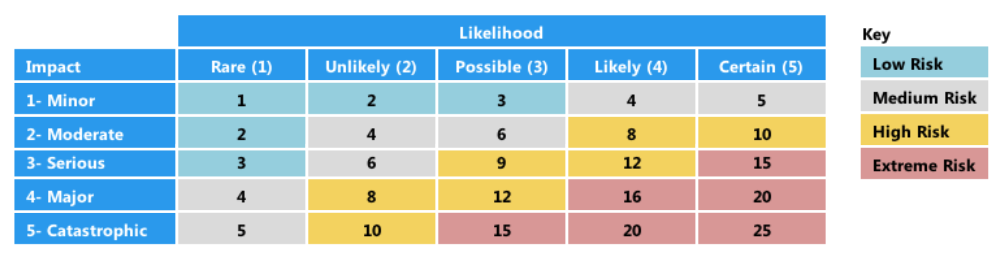
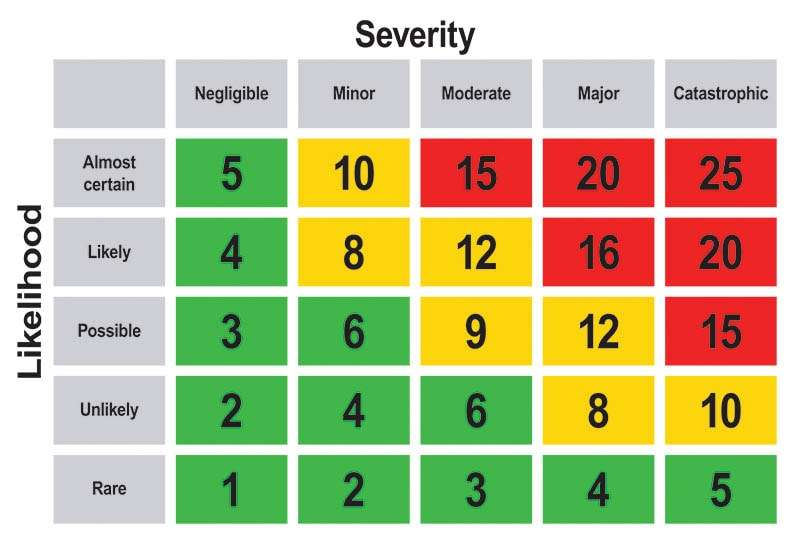
To prioritise risks within the Risk Register, businesses often employ a Risk Score Matrix. This matrix evaluates risks based on two essential factors: Likelihood and Severity.
- Likelihood: This factor assesses how probable it is for a specific risk to occur. Likelihood is usually categorised as rare, unlikely, possible, likely, or almost certain, each with a corresponding numerical value.
- Severity: Severity measures the potential impact a risk could have on the business if it materialises. Impact levels may range from insignificant to catastrophic, with corresponding numerical values.
Each of factors can rated on a scale from 1 to 5, where Likelihood and Severity respectively can be:
- 1 – Rear / Negligible
- 2 – Unlike / Minor
- 3 – Posible / Moderate
- 4 – Likely / Major
- 5- Almost Certain / Catastrophic
By combining these two factors, a Risk Score is calculated for each identified risk. The formula typically used is:
Risk Score = Likelihood * Severity
This numerical value indicates the level of urgency in addressing the risk. The risk score can be color coded. An example of a risk score matrix is indicated below.
Risks with higher scores require immediate attention and robust mitigation strategies.
Effective Risk Mitigation Strategies
After assessing risks using the Risk Score Matrix, businesses can implement appropriate mitigation strategies. These strategies can include risk avoidance, risk reduction, risk transfer, or acceptance.
- Risk Avoidance: Involves altering business practices to sidestep the risk entirely. For instance, discontinuing a high-risk product or service.
- Risk Reduction: Implements measures to decrease the probability or impact of a risk. This might involve enhancing security systems or diversifying suppliers.
- Risk Transfer: Shifts the risk to another party, often through insurance or outsourcing. This strategy is common for risks that cannot be avoided but can be financially mitigated.
- Risk Acceptance: Acknowledges the risk and its potential consequences without taking specific actions. This approach is viable for low-impact risks or those with high mitigation costs.
Conclusion
In today’s volatile business environment, mastering the art of risk management is paramount. By diligently identifying risks, documenting them within a structured Risk Register, and assessing them using a Risk Score Matrix, businesses can navigate uncertainties with confidence. A proactive approach to risk management not only safeguards the business but also fosters resilience and adaptability, ensuring long-term success in an ever-changing market landscape. Remember, in the realm of business, preparation is the key to triumph over uncertainty.